PinBox - User Guide
Version 1, Release 2 (V1R2)
Safe portable storage for your secret passwords!
Contents
This is the primary documentation for PinBox. It contains the following sections:
· Introduction
· Features
· Dialogs
· Properties
· Installation
· Passwords for Files
· About Passwords
Introduction
Passwords (sometimes called a personal identification number, or PIN) are those secret values that you have to create in order to use many of the services provided on World Wide Web (WWW), as well as, a variety of other applications performed on your computer. Of course keeping them secret (i.e., known only to you) is what strong security is all about. As a result you very faithfully adhere to the principles of proper protection by conforming to the following rules:
· You never write them down, they are stored in your mind only.
· You never use real words that might be found in some kind of dictionary.
· They contain some number of non-language characters such as numeric digits and special characters.
· They contain a sufficient number of characters to make trial and error (i.e., brute force) attacks time consuming and expensive even for attackers capable of utilizing a bunch of fast computers.
· And of course, you change them periodically.
It seems reasonable to believe that the above might be practical for a limited number of such values. However, these rules are a bit unpractical for some users of modern information technology. For example, how many services that require you to logon to a website using a password have you registered to use? Typical logon mechanisms force you to create independent accounts with each website provider. Website providers tend to behave as if users are their captives. In that, users only need to use one website which of course is theirs. While this might be desirable from the provider’s point of view it doesn’t fit very well with reality for most people. A consequence of this phenomenon is that, in order to protect themselves, users are expected to store a rather large number of values in their mind. Furthermore, these values must be properly associated with other information pertaining to the logon scenario for all of the applicable websites.
The basic premise for PinBox is that it just isn’t practical for people to clutter up their mind trying to precisely store and retrieve logon information for all of the various entities with which they must deal in this manner. Rather, there exists a need for safely storing these secrets in a manner that they can be easily retrieved when needed. This criteria suggests requirements such as the following:
· Other users must NOT be able to retrieve the secret information from the storage media.
· Passwords should not be commingled with other information (e.g. address books) used for a different purpose. To do so would have the effect of unnecessarily exposing them.
· The storage media needs to be portable –
o It must be practical to carry the media wherever it might be needed.
o It must be practical to easily use the media on different computers.
PinBox addresses these requirements by providing the following:
· All user supplied data is stored in an encrypted database.
· The database contains only information related to the use of passwords.
· The database is designed to reside on removable media (e.g., USB flash memory drive).
· All necessary software is stored on the removable media so as to be useable on any computer that supports the media.
· Software installation on individual computers is NOT done.
PinBox uses terminology that is closely related to the notion of logon accounts maintained by service providers operating on networks. However, passwords with the same properties described above are also used for other purposes. For example, many software products have features that allow passwords to be used for protecting files. Many people, who have files deserving of such protection, are likely to forego the use of these features because they lack an effective means of managing passwords. PinBox can be used to maintain such passwords. For further advice on this refer to the section “Passwords for Files”.
Features
PinBox uses a tabbed pane for displaying the information stored in a database. For example, when the distributed software is first executed you are prompted for the password for a database named “Safe”. If you enter “password” you should be presented with the following view.
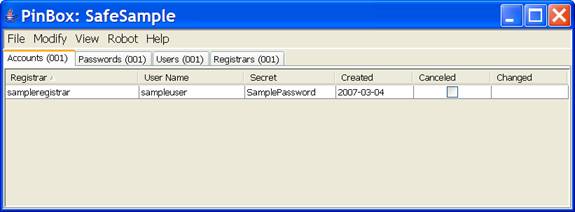
The basic features supported by PinBox are described in subsequent sections as follows:
o Tables
o Apache Derby
o Viewing and Sorting
o Action Menus (File, Edit, View)
o Secure Password Generation
o Copy&Paste or Drag&Drop
o Folding Entered Names
Tables
PinBox uses a relational data base manager (Apache Derby) to store data pertaining to passwords. This database is encrypted using a secret key (also known as a boot password), which you are responsible for assigning and remembering. In return for remembering this one secret you are able to forget all of the passwords stored in it. The software is distributed with a sample database named “Safe” with an initial password that is set to “password”. Whenever you start the PinBox program it will attempt to open (boot) the database that was most recently used. The first time you start the PinBox program this is the “Safe” database that is distributed with the software. The first thing you should do after starting the program is one of the following:
1. Change the boot password (using menu item "File > New > Change PW”) for the “Safe” database base to be a secret assigned by you.
2. Create a new database (using menu item "File > New > Create DB”) with a name other than “Safe” and a secret boot password assigned by you.
PinBox maintains a table for each of the following entities:
Accounts
Passwords
Users
Registrars
Apache Derby
PinBox uses open source database management software produced by the Apache Software Foundation (www.apache.org). You don’t need to know anything about it in order to use PinBox. However, there are a couple of basic concepts that might be helpful for anyone to know about. The first is that Derby stores databases in a collection of files contained in subdirectories of a directory (i.e., sometimes called a folder) referred to as the Derby System Home Directory. The second is that database names correspond to the names of subdirectories contained within the Derby System Home Directory.
The PinBox distribution package contains a subdirectory named “Derby” which contains a subdirectory named “SysHome”. Therefore the subdirectory defined by the path “.\Derby\SysHome”, which is relative to PinBox’s root directory is the default location for databases. Therefore the default database, named “Safe”, included in the distribution package, is contained in the subdirectory named “.\Derby\SysHome\Safe”.
A backup copy of a Derby database can be created by making sure that the applicable database is closed (i.e., not being used) and then simply copying all of the files contained within the respective subdirectory (e.g., “.\Derby\SysHome\Safe”). The use of an archiving tool such as PKzip, 7-Zip, or WinZip provides an excellent method of maintaining backup.
Be sure to keep track of the boot password that is in effect when the backup copy is created. If you should restore from the backup copy this password will be required to boot (open) the database.
Viewing and Sorting
The tables are displayed in a tabbed pane which contains a separate tab for each of the data entities. For each entity you view the corresponding list of elements by selecting the corresponding tab. Each view can be sorted in an order according to the values stored in any of the columns. This is done by selecting (i.e., position pointer and click) on the respective column heading. You can cycle through different sequences (i.e., ascending, descending, not sorted) by successively selecting a column heading.
Note: PinBox normally maintains the tables in ascending order of the column containing the unique element.
Action Menus
Menus are provided for the purpose of controlling actions that can be performed by the PinBox program. A standard menu bar on the top of the screen contains the following menus:
· File
· Modify
· View
· Robot
· Help
In addition, the Browse and Edit actions are also provided on a Pop-up Menu which is raised by clicking the right mouse button.
File
The actions which can be performed are the following:
New – used to either create a new database (“Create DB”) or change the password (“Change PW”) for the currently opened database
Open – used to close the current database and open a different one.
Exit – used to terminate the program.
Modify
These actions apply to the table being viewed (i.e., selected tab) and are used to alter the currently opened database. Those actions that are NOT applicable to the table being viewed are dimmed (i.e., NOT selectable). The set of available actions are the following:
Add – used to add a new element for the corresponding table. Duplicate elements are NOT allowed. The value assigned for a password, user or registrar must be unique. New accounts are created by selecting a value for each of the other previously entered elements (i.e., user, registrar, and password). For accounts, uniqueness is determined by the combination of user and registrar which is selected.
Update – used to change the value assigned for a user, registrar, or password. Accounts are NOT updated. If a mistake is made when adding an account it can be deleted and another one added.
Delete – used to remove the selected account from the database. The account is deleted immediately. No confirmation dialog is displayed but the operation is easily reversed by using the “Add” action.
SelectPW – used to assign a different password to an account by selecting a different value from the list of defined passwords. Selecting a password that is in the revoked state (e.g., see notes below) is prohibited.
Notes:
1. It is generally expected that once an element is created it is never deleted. This is consistent with the way account relationships are defined in the real world. While you may close an account and stop using it, the fact of its existence cannot be undone. PinBox intends to preserve the integrity of the historical record. The “Update” and “Delete” actions are provided because you may make data entry mistakes.
2. For both accounts and passwords a status is maintained which allows you to indicate when an account is canceled or a password is revoked. You can edit (change) these status indicators by selecting the checkbox on the corresponding element for either accounts or passwords. The checkbox behaves as a toggle and the date displayed in the column labeled “Changed” indicates the last (most recent) time that the status was changed.
3. While passwords that are in the revoked state cannot be selected for assignment to an account, it is valid to revoke passwords that are assigned to accounts. Revoked passwords are color highlighted. This makes it easy to identify them for the purpose of selecting another password.
View
These actions are used to either hide or show the values assigned to passwords as follows:
Show PW – used to show (reveal) the values assigned to passwords on the displayed view.
Hide PW – used to hide (mask) the values assigned to passwords on the displayed view.
Note: You can use either copy&paste or drag&drop when passwords are hidden and the correct value is transferred to the receiving input field.
Robot
This action may be used to perform robotic operations. Robotic operations involve the manipulation of other programs running on the same system. These actions are the following:
Browse – used to launch the system browser using the registrar from the selected row as the URL. As such it is only enabled when viewing either the Accounts or Registrar tab.
It seems that there is some inspection of the URL that is performed by the platform specific mechanism used to launch the browser. In some cases this has the affect of preventing the browser from being launched. It has been found that better results seem to occur if the URL always starts with a protocol specification. Therefore the value used (i.e., registrar) is examined to see if it starts with either “http://” or “https://”. When one of these protocol specifications is not found the value “http://” is inserted.
Logon – used to robotically enter (i.e., simulate typing on the keyboard) the user name and password for the selected account. As such it is only enabled when viewing the Accounts tab. To use this feature you must first position the cursor in the input field of another window where the user name is to be entered. Then give the PinBox window focus and select the “Logon” action. PinBox responds by simulating the pressing of keyboard keys as follows:
· “Alt-Tab” key to switch focus to the previously active window.
· Key combinations appropriate for entering the user name.
· “Tab” key to move cursor to the password field.
· Key combinations appropriate for entering the password.
· “Enter” key to initiate the logon.
The above key sequence is commonly, but not always, used for logon to user accounts. Therefore, the desired affect is achieved only when the key sequence described above is valid.
Note: The robotic logon feature has only been tested on computers with US keyboards.
Help
Use this action to display this document with the system’s default browser.
Secure Password Generation
Strong passwords are those that are difficult to crack programmatically even with fast computers. Unfortunately, remembering strong passwords can be unreliable. PinBox attempts to address the problem by allowing you to forget them. Instead it provides you with an easy to use and readily accessible mechanism for maintaining and retrieving your passwords. This contributes to your ability to actually use strong passwords. PinBox also makes it easier to use strong passwords by generating them for you.
Whenever you go to add a new password, the dialog that is invoked generates a value for you. This value is generated using a random number generator that is strong by cryptographic standards (i.e., the Secure Random function supplied by the standard Cryptographic Service Provider supplied as part of the Sun Microsystems JRE). You can either accept this value or replace/modify it to a value of your choice.
The character set used for the generated value is the set of printable characters that Windows supports for passwords. The length of the generated password can be adjusted by modifying a setting in the properties file. Refer to the discussion of properties herein for further details.
Note: It is expected that entering descriptions for passwords is something you might generally not do. However, when using random values for passwords, be aware that the description can help you identify them on the password tab, when you need to revoke or update them.
Copy&Paste or Drag&Drop
You can use the cells in PinBox tables as the source for copy&paste or drag&drop operations with destinations (i.e., target for “paste” or “drop” operations) in other programs. This is most useful for accurately entering logon information.
The Swing Look-And-Feel used by PinBox supports the use of the keyboard for copy&paste but does NOT seem to provide mouse support. The supported keyboard keys are the following:
· Ctl-C - Copy operation
· Ctl-V – Paste operation
A drag&drop operation is done, as you’d expect, by selecting the source cell and then holding the Ctl key down while dragging the mouse.
Folding Entered Names
The names of users and registrars must be unique. However, a difference in case is sufficient to make values unique. Insofar as case is normally not relevant for these values, it is possible to specify that you want all values converted (i.e., folded) to lower case. This has the affect of preventing the addition of multiple names composed of the same sequence of characters that only differ from each other by the case used for some alphabetic characters. This capability is controlled by a setting in the properties file. Conversion to lower case is the default setting. To change this behavior the property file must be updated. Refer to the discussion of properties herein for further details.
Logging
PinBox uses the standard logging capabilities included in Java. The scripts used for starting the PinBox program control what kind of log file is produced. The options are as follows:
· Normal – Only logs exceptions and warning conditions (i.e., events that are not expected to occur).
· Debug – In addition to exceptions and warning, a variety of normal events are also included in the log file.
Dialogs
Dialogs are child windows that open to either display messages or prompt you to enter data. You are not able to interact with the main parent window while a dialog window is being displayed. PinBox uses dialogs when responding to actions requested via menu selections as well as to display informational messages. This section describes some of the most significant dialogs.
Note: On data entry dialogs the “OK” and “Cancel” buttons are mapped to keyboard accelerator characters.
· Alt-O : “OK”
· Alt-C : “Cancel”
On data entry panels, the “Enter” key is NOT mapped to the “OK” button.
Changing the Boot Password
The boot password is a password that you must remember. It is used to encrypt the databases used by PinBox for storing data. The default database named “Safe” that is supplied with PinBox uses the value “password” for the boot password. Since this value is both publicized and well known it is especially important that you change it before using the default database.
When you select the “File > New > ChangePW” action the dialog shown below is used to prompt for the current boot password needed to boot the currently opened database. The name of the applicable database is indicated by the dialog.
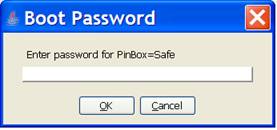
When “OK” is selected the dialog shown below is opened. It is prompting for the new value that is to replace the boot password previously entered. The new value must be entered twice. Once to specify the value and a second time to confirm that it has been entered correctly.
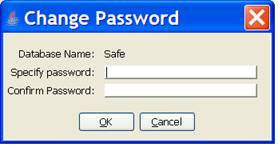
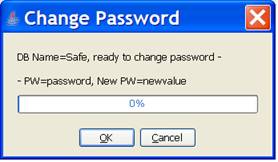
When “OK” is selected the dialog shown below is opened, indicating that PinBox is ready to perform the password change operation on the indicated database using the indicated values for the password and new password. Changing the password involves encrypting the whole database using the newly generated encryption key. The amount of time required to complete the operation depends on the size of the database.
Notes:
1. Successful completion depends on entering the correct value for the current password. If the value entered isn’t correct the “change password” operation will fail after having closed (shutdown) the indicated database. This leaves you without an opened database. The database can then be opened by using “File > Open” menu item and entering the correct value for the password.
2. PinBox prohibits password values that contain whitespace characters (i.e., blank and certain control characters). Furthermore, the value entered for a boot password is subjected to a minimum length (i.e., number of characters) restriction. The default value for the minimum length is “8”. However, this can be changed by editing the properties file (described elsewhere).
The need for changing the boot password pertains primarily to the possibility that your password has been compromised. If you suspect this to have happened you should change the password and destroy any copies (e.g., backups) of databases using the compromised password. Please recognize that changing the password does not affect other copies of the database. Therefore, even though the databases are encrypted, you should endeavor to prevent database/s from being copied by others.
The primary source of protection for your PinBox database/s is the strength of the boot password/s that you assign. The amount of protection you need depends on a variety of factors including the following:
· The extent of the possibility that your database has been obtained by someone you shouldn’t trust. This depends on –
o How many other computers have the subject PinBox database/s been mounted on?
o Who has access to the media used to store your database/s?
· What are the consequences of others having access to your passwords? In that, what damage might you suffer if someone learns the passwords stored in the subject database/s?
Adding Entities
When you add new entities a dialog is invoked for the purpose of prompting you to enter the values for the corresponding elements. The dialog below is the one used for adding new registrars. A similar dialog is used for adding other entities (i.e., users and passwords).
A value must be entered for the “New …” entity but the “Description” field is optional. When entered entity values are trimmed of leading and trailing whitespace characters. The value entered for the new entity must be unique (i.e., different from other entities of the same type). The values for entities must not contain embedded whitespace. Descriptions provide a means for elaborating on the meaning or purpose of the corresponding entity. You should also recognize that these descriptions can be used to sort tables for display purposes. Because of this, a thoughtful scheme for specifying descriptions can be very useful.
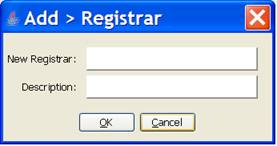
A similar dialog is also displayed for “Update” actions in which case the current values for the related elements will appear in the respective fields. The same rules apply for values entered when updating except that a duplicate entity (i.e., user, registrar, or password) is allowed in order to permit updating of the description field.
The dialog used to add new accounts is shown below. Adding a new account consists of selecting the desired combination of other entities (i.e., userID, registrar, and password). This is done by selecting a value from the respective drop down boxes. As a convenience feature there are also buttons that can be selected to add a new entity directly from this dialog. Selecting one of these buttons will raise the corresponding dialog described above.
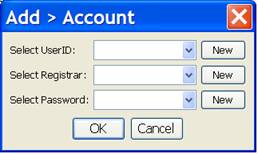
Note: Canceling from the “Add > Account” Dialog does not affect any of the other entities that may have been added by selecting one of the buttons labeled “New”. Whenever “OK” is selected for adding a new entity it is immediately added to both the database and drop-down list of the “Add > Account” Dialog, which makes it eligible for selection.
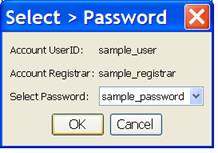
Selecting a Password
You change (select) the password associated with an account by using the dialog below, which is displayed when you select the “Edit > SelectPW” menu item. This dialog is similar to the one used for adding new accounts but limits selection to the password item which you want to associate with the indicated account (i.e., UserID and Registrar).
Accessing Databases
You may never need to exercise these capabilities. PinBox comes with a default database. If you only need a single database you can use it without ever needing to create or open another one. This information is only relevant to those who want to create and open additional databases. To create a new database you need to supply 2 pieces of information. The first is a name for the database. The requirements for a name are that it is different from the name used for any other database within the Derby System Home Directory (refer to the Installation Section for more information about Derby databases). Furthermore, PinBox prohibits values that contain whitespace characters (i.e., blank and certain control characters).
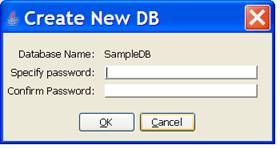
The “Create New DB” dialog begins by prompting for the name to use for the new database as shown below.
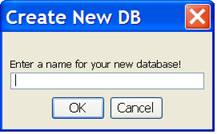
After you’ve provided a valid name for your new database you are prompted for a value to use for the boot password, which is entered twice (i.e., once to specify and again to confirm that you know the value which was specified). PinBox prohibits values that contain whitespace characters (i.e., blank and certain control characters). Furthermore, the value has a minimum length (i.e., number of characters) requirement. The default value for the minimum length is “8”. However, this can be changed by editing the properties file (described elsewhere).
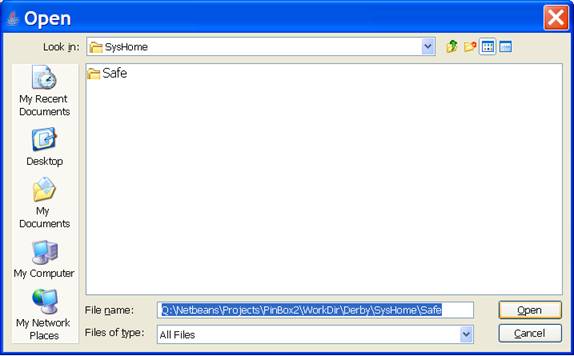
The “File > Open” menu item is used to open a database. The standard Java File Chooser Dialog, shown below, is displayed. Refer to the Section titled “Apache Derby” for information regarding databases. The Java File Chooser is configured to display directories. It is necessary that you only select a directory that corresponds to a database. Selecting other directories will result in an error.
Selecting “Open” after selecting a database directory name will open the “Boot Password” Dialog previously described. Entering the correct password and selecting “OK” causes the database to be opened.
Properties
PinBox uses the standard Java Properties facility for various settings the control how the software operates. Some of these are intended to be set according to end user preferences. The others are intended to allow state information to persist from one execution of the program to another. Therefore, revisions to (i.e., editing of) the properties file named “PinBox.properties” should only be done when PinBox is not running. In that, “Exit” from PinBox before editing the properties file. Those intended for controlling end user preferences are the following:
· PasswordMinLength – Specifies the minimum number of characters that must be entered when specifying the boot password used for encrypting databases. The default value is “8”.
· ConvertNamesToLowerCase – Set to “true” or “false” to specify whether user and registrar names should be converted to lower case. The default value is “true”.
· RandomPasswordLength – Specifies the length used for generated passwords. The default value is “10”.
Installation
PinBox is written in pure Java which means that it is capable of being run on many different platforms (i.e., types of computers). However, in order to prevent problems when attempting to run PinBox on different computers, the package includes a complete Java Runtime Environment (JRE). This JRE as well as some of the surrounding startup scripts are platform dependent. The only platform presently supported is Windows. PinBox has been developed and tested for use on Windows 2000 and Windows XP. It is presumed to work on subsequent versions of Windows.
PinBox is distributed in the form of a self-extracting archive utilizing relative path. The archive includes the following:
· PinBox software
· Starter database named “Safe” with password of “password”
· Apache Derby database management software
· Sun Java Runtime Environment (JRE)
· Properties files to –
o specify PinBox settings
o define settings for logging (normal and debug)
· Scripts for starting the PinBox Program
o Preferred scripts –
1. StartNormal.js : Start PinBox with logging of errors only
2. StartDebug.js : Start PinBox with verbose logging
o Desperation scripts that likely require some alteration are supplied for use on systems where Windows Script Host (WSH) doesn’t allow the use of “jscript”–
1. StartNormal.cmd : Start PinBox with logging of errors only
2. StartDebug.cmd : Start PinBox with verbose loggong
A fundamental concept employed by PinBox is that it can be executed on multiple computers without requiring separate installation on each computer. Therefore, there is no installation program to run. Installation consists only of extracting the files from the archive used for distributing the software package. This is done by executing (e.g., open, launch, or double click) the self-extracting archive. The extraction operation prompts for a subdirectory in which the files should be restored. The files can be stored anywhere on the file system of the target computer that supports output (i.e., ability to write to the database/s). It is ideal to place the files on portable media (e.g., a flash memory drive). This allows a self contained working system to be easily carried from place to place and used on any computer with USB support.
PinBox can be executed by launching one of the supplied startup scripts, which are named “StartNormal.js” and “StartDebug.js”. These scripts are located in the subdirectory for executable files (i.e., “.\Exec”). These scripts depend on the structure of the subdirectories contained in the distribution package. Therefore, the subdirectory structure should not be changed.
As distributed, only one instance of PinBox can be run (started) at a time. However, it is very easy to prepare the operational file system to run multiple instances simultaneously. Insofar as a database can only be used by one instance of PinBox, running multiple instances of PinBox is only useful when you have multiple databases. For each instance of PinBox that you want to run you must create another copy of the executable files (i.e., those contained within the subdirectory named “.\Exec”). Therefore, you simply need to copy all of the files in the “.\Exec” subdirectory to another subdirectory with a name of your choosing. This new subdirectory must also be contained directly within PinBox’s root subdirectory. You can then start an instance of PinBox by launching the startup script from within each of the executable subdirectories.
Note: Trying to start a second instance of PinBox (i.e., launching the startup script from the same executable subdirectory without exiting from a previously started instance) will result in an error. This error can occur when a previously executed instance of PinBox was not properly closed (e.g., system crash). To correct this problem, when you know that another instance is not running, simply delete the file named “PinBox.objects” from the respective executable subdirectory (e.g., “.\Exec”). Because the window location persists from one execution to the next it is possible, when moving from one computer to another, that the window location does not fit within the bounds of the display device. This problem can also be corrected by stopping PinBox (e.g., using Task Manager) and deleting the “PinBox.objects” file.
In situations where the host computer does not support the execution of scripts written in the “jscript” language, a pair of similarly named batch commands (i.e., “StartNormal.cmd” and “StartDebug.cmd”) are provided. These commands will probably require some tailoring for the target computer. This consists of specifying the drive letter and possibly the path needed to locate PinBox’s root directory. This is done either by modifying the command files or invoking them with appropriate parameters (refer to remarks in the command files for details).
Passwords for Files
The passwords you can use to protect files have pretty much the same characteristics as those used for server logon. Therefore, the concepts underlying the design of PinBox can be adapted to this purpose. Some ideas you might want to consider are the following:
· The file is an entity with properties similar to a registrar. For example, the password is usually stored in the file. Therefore, you may want to record file names in PinBox as registrars.
· Typically, there is NO notion of associating a password with an identified user. However, by defining one or more (dummy) user names for association with files the following can be achieved:
o Distinguish accounts created for files from those used for logon.
o Use the sorting features to display a set of multiple files together when viewing the account tab.
· The “copy&paste” feature allows passwords to be accurately input to the target software. This can be done both when assigning the initial password as well as on subsequent reentry.
· Consider using the secure password generation feature to assign strong passwords.
Depending on the number of files in relation to the number of other accounts, it might be desirable to create one or more separate databases for maintaining the accounts associated with files.
About Passwords
Passwords are pretty much meaningless by themselves. They have to be associated with something in order to be useful. The most common association involves combining them with an identifier. This is most typically the identification of a person (i.e., user) but could also include other kinds of objects such as files. The combination of the identifier and the password is then used to determine the authenticity of a request to use a service or object. In order for the service provider to use this information to determine the authenticity of service requests it is necessary to perform some kind of registration operation as a precondition for using the service. The term account is often used to refer to the result derived from the registration operation. Therefore, when referring to passwords, the following terms are especially relevant:
· User – A person who is identified by a distinct (i.e., unique) name within the authority of a registrar.
· Registrar – An entity that enrolls users for the purpose of creating an account relationship.
· Password – A secret value known only by the user that is then used to verify the authenticity of the user.
· Account – Relationship represented by the combination of a registrar and corresponding user. A password is also assigned for each account.
PinBox provides the means for maintaining these relationships using modern database technology combined with an interactive graphical user interface.
Users
The notion of a system abstraction that describes end users has slightly different ramifications depending on whether you view it from the perspective of the person or the service provider.
From the viewpoint of a person it is often most desirable to have a single name by which you are known to any/all service providers. Furthermore, you’d prefer the name to be short and easy to pronounce. It is also good if the spelling is easy to deduce from the pronunciation.
On the other hand, a service provider begins with the basic requirement to assign names to users that uniquely identify them in relation to all of their other users. A secondary objective is to minimize the cost of registering new users.
With the above in mind it is expected that people will use the same user identification on multiple accounts. However, because service providers typically operate independently any particular name may already be assigned to another person. Therefore, everyone is pretty likely to be known by multiple names. However, they will probably try to minimize proliferation, which means they will have relatively fewer names when compared to the number of registrars.
Registrars
As it turns out, typical mechanisms used on the WWW are often very casual (i.e., imprecise) in their approach to identifying registrars as well as service providers for that matter. This shortcoming is a bit curious when considering that the purpose of logon is to provide security. Unlike email services, the logon procedures used by most websites completely ignore the identity of the registrar. They seem to rely on (i.e., trust) that their users have found their way to the correct website. Unfortunately, it is incredibly simple for mischievous parties to provide a service that masquerades as that of a legitimate provider. Given the variety of navigational techniques used to steer people to a website this lack of formality presents a serious security exposure that affects most WWW websites. Fortunately, it is difficult to fake the actual delivery of the most critical services. Logon of course is the exception because it is easy to fake. Therefore, all WWW users are advised to positively confirm the legitimacy of websites to which they’ve successfully logged on. This can be done by confirming that an accessed website can provide information that is only known by the legitimate service. You need to be suspicious of any situation where you successfully logon but are unable to obtain information that can only be provided by the legitimate service provider. Of course, it is true that the whole idea of logon is to establish legitimacy before allowing use of the service. While this is possible, it is almost never done on the WWW.
Irrespective of the weaknesses in typical logon procedures it is necessary for people to keep track of their accounts. To do so means having a way to identify the registrar. Unfortunately, the lack of formality used on the WWW forces people to develop an informal method of their own. A suggestion that seems as good as any is to associate registrars with domain names when dealing with websites.
Passwords
Passwords are secret values associated with accounts that are used for the purpose of verifying the authenticity or legitimacy of service requests. This is often done using a logon procedure. To serve the intended purpose of providing security, passwords need to be protected from disclosure to others. However, in practice it is relevant to question how much security is needed and who is being protected by the security. A simple fact is that many websites demand the use of a logon password for things that don’t require any security. In fact, it is often done in cases where people would prefer, and in fact do choose, to remain anonymous by refusing to provide genuine information concerning their personal identity. Another unfortunate phenomenon is that many service providers have come to believe that enforcing rules on the formulation and maintenance of passwords has the affect of mandating stronger security. This belief is quite shortsighted. It fails to recognize the burden imposed on people who have to deal with many services enforcing different rules. The affect is much more likely to provoke users to compromise the basic principles of password protection mentioned previously. In many situations, it also fails to consider who is being protected. In those situations where it is the user who needs to be protected it is quite unreasonable for a service provider to interfere with their ability to do it according to their personal preference.
Given that the need for security ranges considerably for different accounts there is no one-size-fits-all approach to the matter of password formulation and maintenance. This means that passwords may or may not be shared between different accounts under different circumstances. Therefore, the formulation of a password should properly be viewed as being independent from the association with an account. The assignment of a password to an account should consider a variety of factors, such as the following:
· What strength of security is appropriate for the account?
· How often is the password going to be used?
· What rules are enforced on the password (e.g., for expiration and/or formulation)?
It must also be recognized that changing passwords (i.e., assigning a different value) is something, which typically happens on a per account basis. In that, assigning a different password for one account does not affect other accounts.
Accounts
As used herein an account refers to the enrollment of a user by a registrar. This combination of user and registrar must be unique. In that, the notion of multiple accounts with the same combination of these names is invalid. Be aware that while the combination of user and registrar define an account with respect to PinBox, the unique value assigned to designate the registrar is assigned by you and is typically not used anywhere else. Its only purpose is to allow you to keep track of the entities with whom you have such relationships. On the other hand the userID is typically used, for the purpose of authenticating the party requesting access, during preliminary processing activities such as logon protocols.
A really bad idea that many service providers have adopted is the use of an email address for identifying their users. This amounts to reusing another registrar’s account (as defined above) for their own. This bad idea gets even worse when the service provider attempts to rely on the user identification for communicating with the owner of the account. Consider that email addresses (i.e., accounts) are not permanent. The idea that people should coordinate the change of an email account with an indefinite number of other accounts is extremely impractical if not impossible. Furthermore, while it should be considered bad practice there is nothing that prevents a cancelled (discontinued) email address from being subsequently assigned to another person. This introduces the possibility that the user identification for your account actually belongs to another person. This all becomes quite troubling when you are confronted with the need to recover your secret password by requesting the service provider to send it to an email address that is no longer yours and could possibly have been assigned to another person.